Anonos is not related to or endorsed by the European Union Agency for Cybersecurity - ENISA. REFERENCES TO ENISA DO NOT INDICATE ANY RELATIONSHIP, SPONSORSHIP, OR ENDORSEMENT BY ENISA. ALL REFERENCES TO ENISA CONSTITUTE NOMINATIVE FAIR USE UNDER APPLICABLE TRADEMARK LAWS. For more information about ENISA,
click here.
- The ENISA technical reports referenced on this page analyse different technologies that could be applicable for pseudonymisation (with their advantages and disadvantages), together with practical examples that can help the reader understand possible uses in diverse cases. The reports provide general conclusions, as well as recommendations to all relevant stakeholders for further actions in the field of pseudonymisation.
- While the reports have been created with the contribution of external experts from regulatory authorities and research institutions, they constitute independent work of ENISA. They have not been formally endorsed by any national or EU governmental bodies.
- Each of the ENISA reports include the following legal notice: NOTICE MUST BE TAKEN THAT THIS PUBLICATION REPRESENTS THE VIEWS AND INTERPRETATIONS OF ENISA, UNLESS STATED OTHERWISE. THIS PUBLICATION SHOULD NOT BE CONSTRUED TO BE A LEGAL ACTION OF ENISA OR THE ENISA BODIES UNLESS ADOPTED PURSUANT TO THE REGULATION (EU) NO 2019/881. THIS PUBLICATION DOES NOT NECESSARILY REPRESENT STATE-OF THE ART AND ENISA MAY UPDATE IT FROM TIME TO TIME. THIRD-PARTY SOURCES ARE QUOTED AS APPROPRIATE. ENISA IS NOT RESPONSIBLE FOR THE CONTENT OF THE EXTERNAL SOURCES INCLUDING EXTERNAL WEBSITES REFERENCED IN THIS PUBLICATION. THIS PUBLICATION IS INTENDED FOR INFORMATION PURPOSES ONLY. IT MUST BE ACCESSIBLE FREE OF CHARGE. NEITHER ENISA NOR ANY PERSON ACTING ON ITS BEHALF IS RESPONSIBLE FOR THE USE THAT MIGHT BE MADE OF THE INFORMATION CONTAINED IN THIS PUBLICATION.
- THE “50 BEST PRACTICES” REFERENCED ON THIS WEBSITE WERE INDEPENDENTLY DEVELOPED BY ANONOS USING CONTENT CONTAINED IN THE ENISA REPORTS. THEY DO NOT CONSTITUTE TECHNICAL OR LEGAL RECOMMENDATIONS OF ENISA.
GDPR Pseudonymisation: State-of-the-Art Technical & Organisational Controls to Achieve Functional Separation
Click below to download a spreadsheet to compare the capabilities of different vendors to comply with 50 Best practices for GDPR compliant Pseudonymisation.
View Vendor Comparison Matrix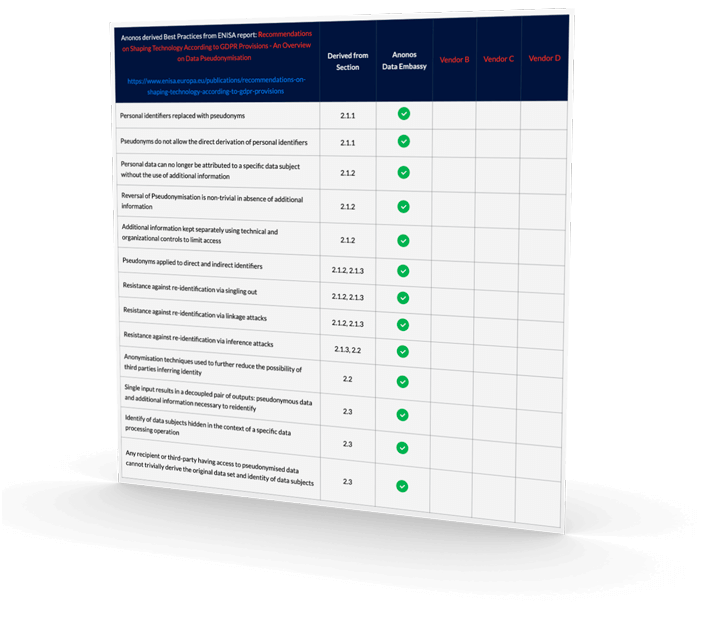
ENISA’s mandate is to enhance existing expertise in member states by supporting the development of cross-border communities committed to improving network and information security throughout the EU.
We recommend the following ENISA reports on Pseudonymisation:
We recommend the following ENISA reports on Pseudonymisation:
- Pseudonymisation techniques and best practices
- Recommendations on shaping technology according to GDPR provisions
- Data Pseudonymisation: Advanced Techniques and Use Cases

© 2024 Anonos. All rights reserved. Privacy Policy
